Today the FBI just announced, cyber criminals (which are easily recognizable according to the news and many websites for their predilection to wearing hoodies even in the summer) "are using search engine advertisement services to impersonate brands and direct users to malicious sites that host ransomware and steal login credentials and other financial information." Well, there are two parts for that:
Search engine advertising services
We are talking here about Search Engine Optimization (SEO), where you do magic tricks to move your website as close to the top search results since most people will not look more than 2 search page results for something. There are thousands of companies who make money helping businesses with this, including courses, Ez-Button products, and services ("give your url, what do you think you do, and we will take care of the rest for a price). What they are mentioning here is weaponization of that, which has been known as SEO poisoning since 2020. An example of that is when it was used to distribute BATLOADER malware.
Brand Impersonation
This is a traditional phishing tactic and relies on techniques such as (not exhaustive list):
- typosquatting, which creates a fake website whose domain sounds close enough (within a typo or two) to that of a well known website. They pray on people like me, who mistypes a lot: if the browser returns a page that looks like the one victims expect instead of an error page, they may never noticed they are in the wrong site. This kind of attack is old enough -- yet still quite effective -- to be metioned in the 1999 Anticybersquatting Consumer Protection Act (ACPA)
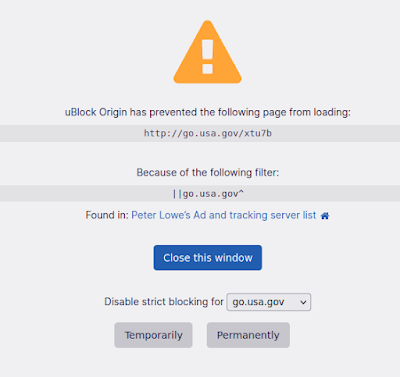
- URL Shortening, which converts long descriptive links into short sometimes cute ones that provide you no idea of where they really came from. Good ad blockers will check these links against lists of known spammers and block them, as shown in the picture below where UBlock origin does not allow a shortened url identified by the Perter Lowe's list of known domains serving ad content, tracking users, spyware servers, and occasionally malware and other nasty purposes.
- IDN homograph attack, an attack where tsome of the characters in the url of a website are replaced by similar (think 1 vs l) characters, or those from a different alphabet that look the same in a HTML-formatted email. As a result this can be seen as a more sophisticated version of typosquatting.
Is this a new form of attack?
Nope.
Are ad blockers enough to stop this kind of attack?
There are no magic pills. They can only do so much. I recommend stopping and checking the url for a search engine result that smells suspicious. Some of the attacks mentioned above -- typosquatting and homograph -- can even be stopped by pasting the url in a proper text editor (think Notepad for windows or vim in Linux) that will not try to import fonts, and then just looking at them. With that said, I do use UBlock Origin myself; the picture on the top of this article is mine.
Should I panic and flail my arms while running in circles?
You could; if you do, make a video of it.
Do you have links for those apps/extensions you mentioned?
- UBlock Origin: This is the one I myself use with Chromium and Firefox. The official source repo site has links to where to get it for those browsers plus Microsoft Edge, Google Chrome, Opera, and Firefox for Android.
- Adguard for Safari: UBlock Origin no longer works with Safari (last version was Safari 13) since Apple disabled Safari extensions as extensions. Those were replaced with a new "extensions framework" which only allows "content blockers", links bundled as an app which Safari enforces. The next best thing for Safari is Adguard, which is recommended by the UBlock Origin team.